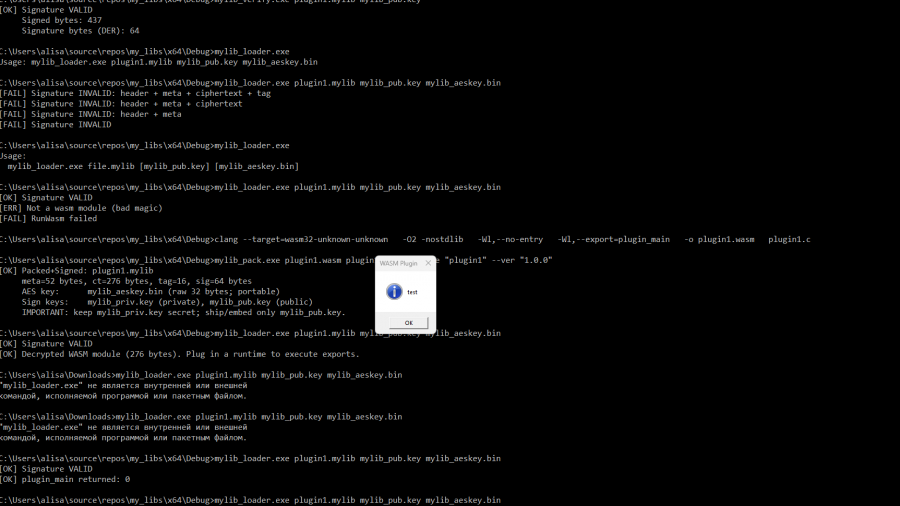
libraries for packaging, verifying, decrypting, and executing WebAssembly plugins packaged in a custom container format .mylib (version 2).
Exploring Protected Process Light and Exploits
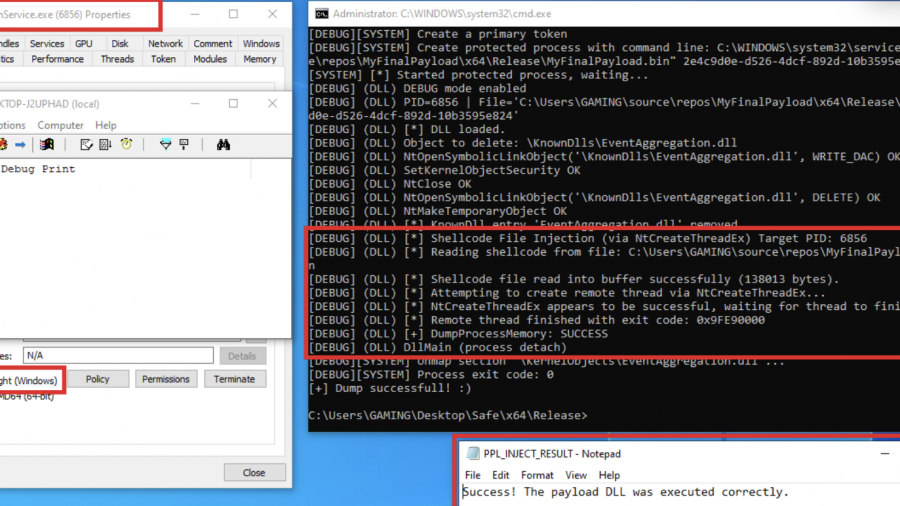
Red team technique—process injection—and how to leverage it against Protected Process Light (PPL)
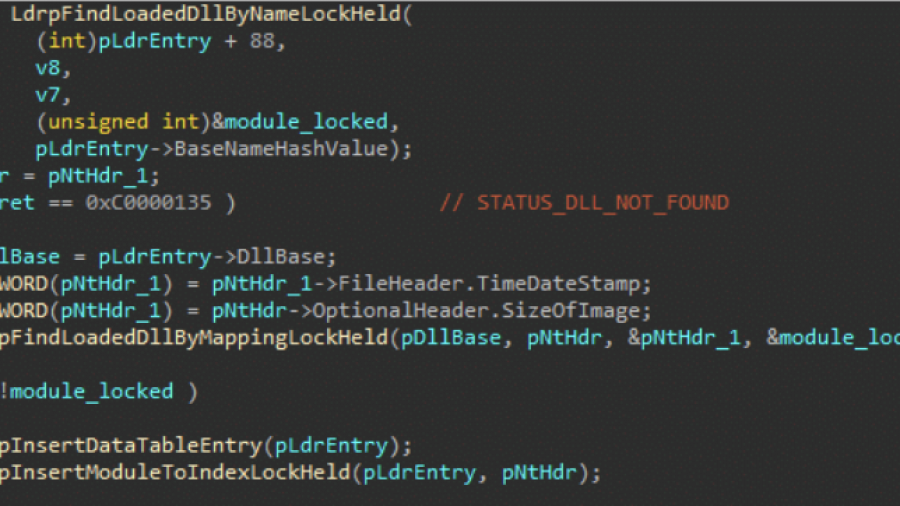
Bypassing Image Load Kernel Callbacks
The post explores how Windows security products use kernel image load notifications to monitor when executables and DLLs are loaded by the system. These callbacks are typically registered via kernel drivers and provide telemetry that defenders use to detect malicious activity. The article analyzes how the standard Windows loader triggers these callbacks deep within NtMapViewOfSection and explains why simply avoiding the kernel event is difficult with limited privileges.