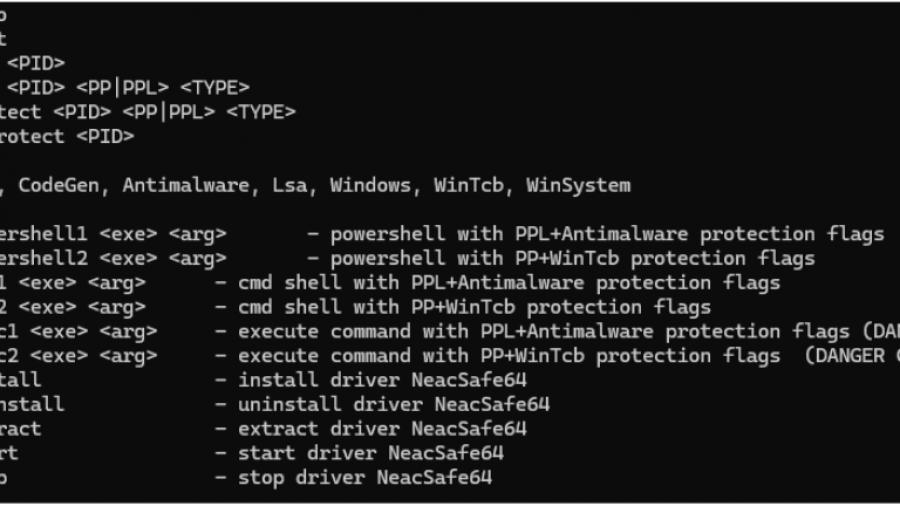
PPLControlShells (the ppexec console tool) is a native Windows PP/PPL experimentation and control utility (x64)designed to help researchers understand, test, and demonstrate how Protected Process (PP) and Protected Process Light (PPL) behave on modern Windows (10/11 + compatible Server builds).
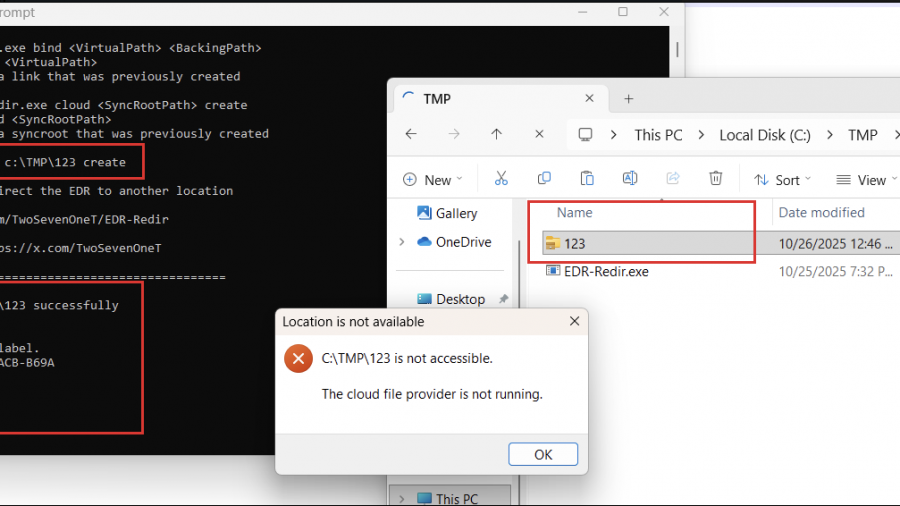
Using EDR-Redir To Break EDR Via Bind Link and Cloud Filter
the technique of exploiting the Bind Filter driver (bindflt.sys) to redirect folders containing the executable files of EDRs to a location that I completely control.